- Home
- Single Post
Ransomware Trends Detected Across National Networks
Ransomware Trends Detected Across National Networks
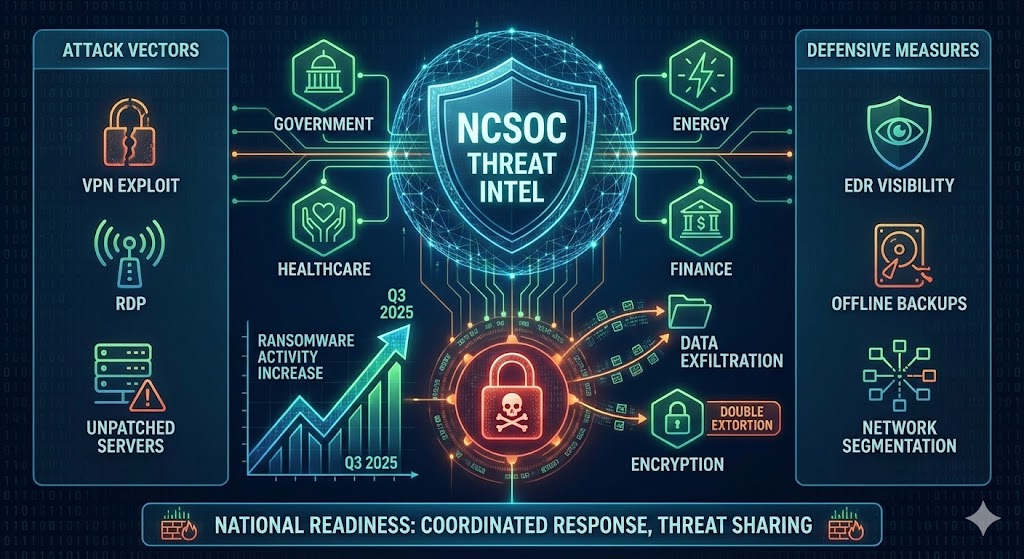
The National Cyber Security Operations Center (NCSOC) has identified a significant rise in ransomware activity across multiple government and critical infrastructure networks in Q3 2025. Recent threat telemetry indicates the use of advanced ransomware families that now integrate data exfiltration and evasion capabilities, posing severe operational and reputational risks to public and private entities alike.
Why National-Level Entities Are Being Targeted
Recent ransomware campaigns have evolved from opportunistic attacks to highly targeted operations. Attackers now prioritize institutions handling sensitive citizen data, essential services, or financial transactions. Sectors such as energy, healthcare, and municipal administration are being exploited for maximum disruption. These attacks often exploit misconfigured VPNs, outdated operating systems, and unpatched public-facing servers.
How These Ransomware Campaigns Operate
These campaigns typically begin with spear-phishing emails or exploitation of remote access interfaces such as RDP and VPN gateways. Once infiltrated, ransomware payloads encrypt network drives and exfiltrate sensitive data to attacker-controlled servers. Modern variants employ “double” and “triple” extortion - demanding payment not only for decryption but also to prevent data leaks or subsequent DDoS attacks. Encryption keys are often rotated dynamically, complicating incident response.
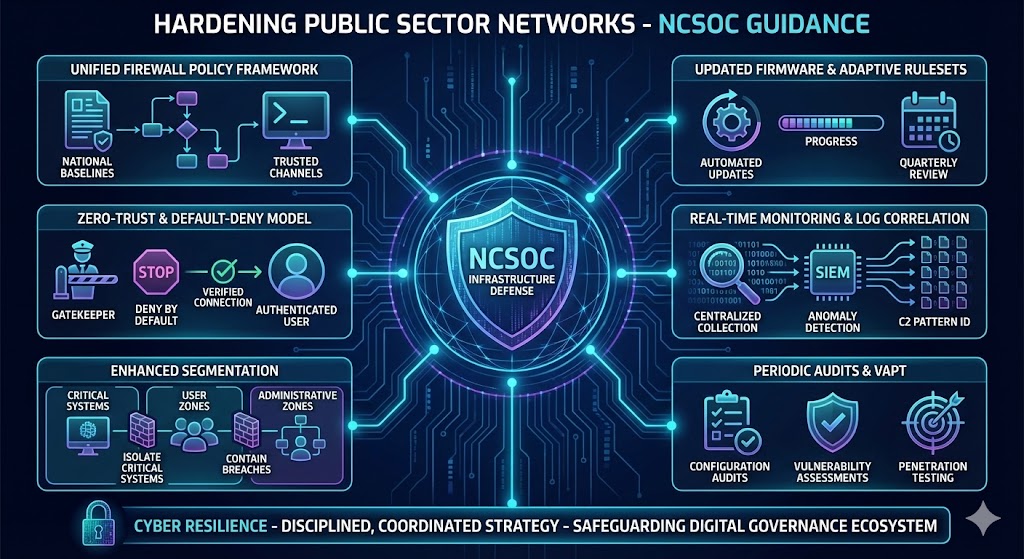
National-Level Defensive Measures
The NCSOC recommends a coordinated defense approach across all connected entities. This includes enforcing endpoint detection and response (EDR) visibility, maintaining offline encrypted backups, applying strict network segmentation, and ensuring operating system and software patches are up to date. National monitoring teams are advised to review indicators of compromise (IoCs) associated with the current ransomware campaigns and enable centralized alert correlation for early detection.
Continuous intelligence sharing through the NCSOC Threat Portal and regular red-team exercises have proven effective in improving response time and limiting lateral movement within infected environments.
- NCSOC Threat Response Unit
Conclusion: Strengthening National Readiness
Ransomware has evolved from isolated criminal activity into a persistent national threat. Continuous vigilance, secure network architecture, and coordinated incident reporting through NCSOC are essential to maintaining cyber resilience. Early containment, forensic visibility, and proactive patching remain the most effective countermeasures against large-scale ransomware operations.
Categories
- Network Security
- Threat Detection
- AI & Automation
- Compliance
- Industry News
Related Posts