- Home
- Single Post
Best Firewall Practices for Safer Networks
Hardening Public Sector Networks Against Modern Threats
With the expansion of government digital infrastructure and citizen-facing services, securing public sector networks has become a national priority. The National Cyber Security Operations Center (NCSOC) emphasizes that consistent firewall hardening and policy enforcement are essential to preventing intrusions, lateral movement, and data exfiltration attempts targeting critical systems.
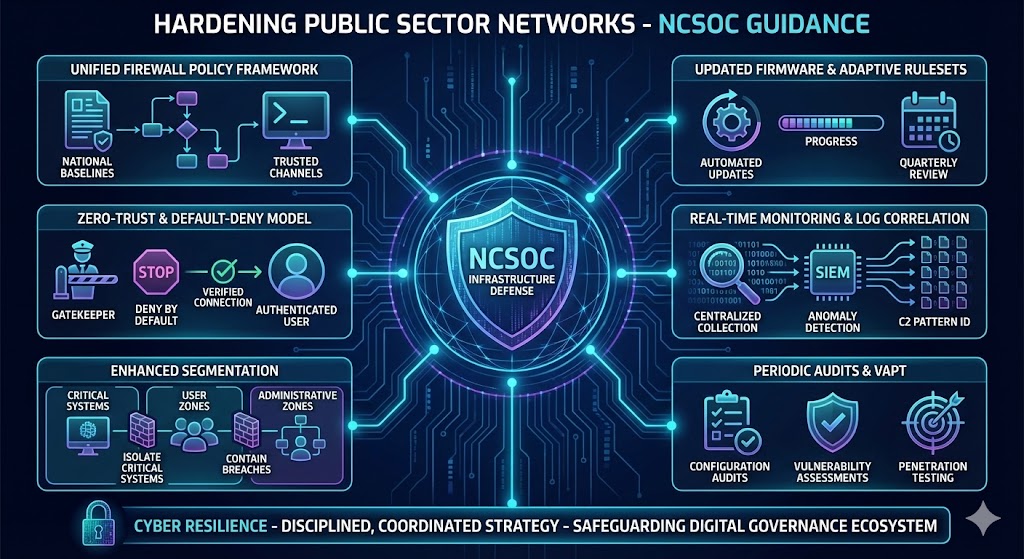
Establish a Unified Firewall Policy Framework
Every ministry, department, and provincial network should operate under a clearly defined firewall policy aligned with national cybersecurity baselines. This policy must specify approved communication channels, trusted IP ranges, and escalation protocols for incident response. Standardizing these controls reduces misconfigurations and ensures consistency across distributed public networks.
Implement a Zero-Trust and Default-Deny Model
All government firewalls should enforce a “deny by default” rule, permitting only explicitly authorized traffic. Adopting a zero-trust model-where every connection must be verified-helps prevent lateral movement even if one node is compromised. This approach limits potential exposure from phishing-based credential misuse or remote exploitation attempts.
Maintain Updated Firmware and Adaptive Rulesets
Outdated firewall firmware and static access rules increase risk exposure. Administrators must apply vendor security patches promptly and review rulesets quarterly to align with evolving threats. Automated update scheduling and configuration backups should be part of every agency’s standard operating procedure.
Enhance Segmentation for Critical Environments
Implement network segmentation to isolate critical systems from user and administrative zones. Using internal firewalls, separate databases, control servers, and application layers to contain potential breaches. Segmentation also supports rapid containment during ransomware or insider activity incidents.
Enable Real-Time Monitoring and Log Correlation
Centralized firewall log collection through the NCSOC SIEM enables early detection of anomalies, policy violations, and scanning behavior. Correlating firewall events with endpoint and DNS telemetry helps analysts identify command-and-control patterns or brute-force attempts before escalation.
Joint audits between NCSOC and institutional IT teams have shown measurable improvements in firewall integrity following centralized rule validation and regular cross-sector threat simulations.
- NCSOC Infrastructure Defense Team
Conduct Periodic Configuration Audits and VAPT
Scheduled firewall configuration audits and vulnerability assessments are critical for identifying legacy rules, unused ports, and shadow policies. Annual penetration testing should validate both perimeter and internal firewall effectiveness. These proactive evaluations strengthen the nation’s overall cyber resilience and help ensure compliance with emerging regulatory frameworks.
By following these hardening measures, public institutions reinforce their ability to detect, contain, and recover from modern cyber threats. A disciplined, coordinated firewall strategy under NCSOC guidance is fundamental to safeguarding Sri Lanka’s digital governance ecosystem.
Categories
- Network Security
- Threat Detection
- AI & Automation
- Compliance
- Industry News
Related Posts